- What Is API?
- What Is API Testing?
- What Is POSTMAN?
- What Are The Basics Of POSTMAN?
- An API Request’s Workflow in Postman
- What Are The Testing Concepts?
- Authentication
- Authorization
- Common Web Vulnerabilities
- Postman Traffic Proxying by Burp
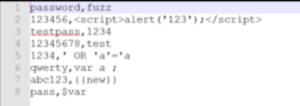
- Example – test.csv
- How To Implement HMAC In Postman?
- Examples Of pm.request Functions:
- Summing up!
Today, API testing approaches in software testing are becoming highly popular because of the massive amounts of data being shared and transferred among various systems and apps. Due to its accuracy, API testing not only significantly increases the effectiveness of your overall testing approach as a whole but also speeds up the delivery of your program.
This blog will discuss the definition and scope of API Security testing.
What Is API?
The Application Programming Interface is a computing interface that allows two separate software systems to communicate and exchange data. Any software system implementing an API Development includes several functions/subroutines/features that another software system can use to communicate. API defines many things between two software systems, such as how to make requests, requests that can be made, data formats that can be used, and so on.
What Is API Testing?
API testing software analyses and validates an API to ensure that it meets its expected functionality, security, performance, and reliability. In API Testing, rather than the standard inputs and outputs we use daily, the software is used to send calls, get the result, and not down the system’s response. API tests are performed either directly or as part of integration testing.
API tests are distinct from GUI tests in that they do not focus on the appearance and feel of an application. They primarily focus on the software architecture’s business logic layer, application security, and data responses.
These tests are typically performed by sending requests to one or more API endpoints and comparing the results to the expected ones. API testing is frequently automated and used by DevOps, quality assurance (QA), and development teams for continuous software testing.
What Is POSTMAN?
Many developers use Postman to document, test, and interact with Application Programming Interfaces (APIs). With the usage of various APIs in web, mobile, and other applications. This can be a helpful tool for a security tester or developer to assess the API’s security posture.
We will explore the fundamentals of using Postman, including explaining the main components and features. It will review some security testing use cases, such as data-driven tests for parameter fuzzing and the Postman Sandbox JS execution environment for HMAC Header Implementation. Its primary function is for functional testing, interacting, and documenting the API rather than security analysis. This article can be used as a beginner’s guide to using Postman as a useful security tool.
Postman is mostly used for testing and interacting with RESTful API. RESTful APIs are built on representational state transfer (REST) technology, an architectural style and approach to communication that employs the HTTP verbs GET, PUT, POST, and DELETE to implement CRUD (Create, Retrieve, Update, and Delete) operations on objects/data.
The Postman tool primarily focuses on REST API communication via JSON, a lightweight data-interchange format and the preferred method of communication in REST API. However, it can also work with most other data types.
What Are The Basics Of POSTMAN?
Postman began as a Chrome application but has since evolved into a fully native application. The software is available for Windows, Mac, and Linux download at https://www.getpostman.com/apps.
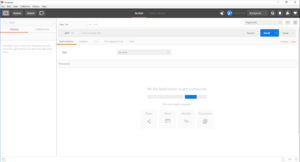
The app’s user interface (UI) is simple; we can create an API request from scratch or import a Postman collection or a CURL command, a common way to define complete HTTP Requests.
The following are a few concepts that a new app user should be aware of.
Collections:- In Postman, collections are used to group similar individual API requests. Users can share the collection with each request’s relevant headers, body, URL parameters, authorization configurations, and description. Exporting the collection can benefit onboarding a new developer or providing complete scoping details and mock request data to a security tester. Postman allows you to share collections online by providing a link.
Runner:- When you submit requests from a collection one after another, you are essentially running the collection. You may create workflows that reflect your API use cases using scripts, transfer data between API queries, and construct integration test suites.
Variables:- In Postman, variables function similarly to variables in regular programming. There are various ranges for variables. The scopes are Global, Collection, Environments, Local, and Data, going from wide to specific. Variables can be accessed through the request’s URL, Body, or Headers.
Environments:- Environments keep the variables as a collection of key-value pairs. Environments can be compared to the API requests’ contexts. For instance, if an API request is being made by numerous users, each of whom has a unique API-Key, we may switch between users by changing the environment and using the same variable, {{“API-key”}}, which is stored in each environment.
Pre-Request Script:- You may use pre-request scripts to set up any data or variables in the request or to test the response.
Tests are executed when the API request response has been received. The Response Code, Cookies, and Body are among the response details that scripts developed here can interpret. Tests have a pass/fail outcome, such as whether the return code is 500.
An API Request’s Workflow in Postman
Pre-Request Script → Request → Response → Test
Start by choosing the HTTP verb and entering the Request URL to create an API request (API End Point). There are sub-tabs for filling out the appropriate Headers (such as Basic, OAuth, and AWS Signature) and the Request Body (if needed). Form, form-URL-encoded, raw data (text, JSON, XML), or binary data can be used as the request’s body. The response is displayed in the app’s bottom part when an API request is made.
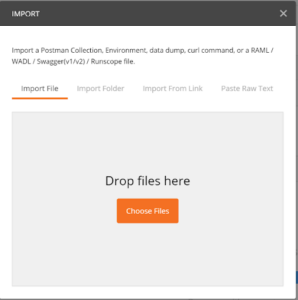
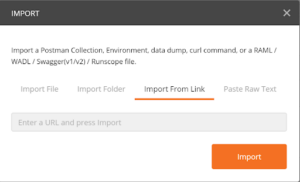
Importing collections is the fastest method to begin using Postman. Postman allows you to import collections by pasting a CURL command, a Postman collection link, a Swagger file, or a JSON file (Swagger file or Postman Collection file).
Importing Collections
File → Import
Figure 2: shows how to import collections by dragging and dropping the Swagger or Postman JSON files.
Figure 3: illustrates importing API requests by copying the common Postman Collection link.
It’s quite easy to test and use REST APIs when using Postman. It can interact with many types of data, various authentication protocols, and import and export API Collections. Postman makes it simple to find parameters that need more investigation and is beneficial for logical testing of the API by offering a clear UI to compose requests, set up authentication, and import API collections. In the following blog post, I’ll go into more detail on using Postman to verify API security.
What Are The Testing Concepts?
Authentication
There are many ways to implement authentication in APIs, including using Basic, cookies, tokens (JWT, OAuth2), etc. Testing must, at the very least, confirm that authentication controls are being implemented correctly. Working with cookies, tokens, client certificates, or other authentication systems is quite simple using Postman.
Authorization
APIs can send and receive sensitive data and use standard HTTP methods like PUT, DELETE, or GET. Proper permission measures must be implemented to prevent unauthorized access to sensitive data.
Common Web Vulnerabilities
Many of the usual flaws in online applications, such as cross-site scripting (XSS), injections, error exposes, etc., can be carried over into API. It is crucial to comprehend the context in which the API will be utilized to identify the kinds of vulnerabilities that might be present.
Postman Traffic Proxying by Burp
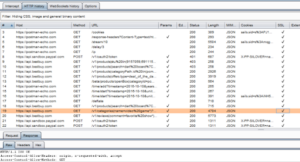
A strong security toolchain must be configured to test API’s effectively. To give complete testing coverage for the API, Postman can proxy API traffic through well-known security testing tools like Burp. Burp’s features, including Scanner, Intruder, Repeater, etc., can be used this way.
Step 1: Launch Burp and configure TCP port 8080 as the listener (or any unused local port)
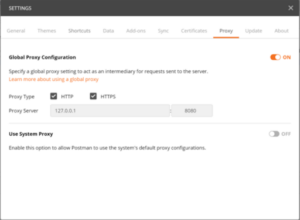
Step 2: Configure Postman to use the local Burp listener as its proxy.
Figure 1: The Proxy subtab in Postman Settings
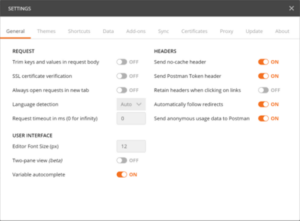
Step 3: To avoid “Self-signed Certificates Blocked” warnings, disable SSL certificate verification in Postman’s settings under the General subtab.
Figure 2: General subtab of Postman Settings
Figure 3: Burp Scanner’s capture of Postman traffic
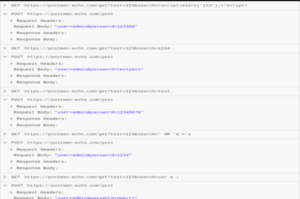
Fuzzing Parameters with Postman’s Collection Runner
To run specific kinds of security test scenarios, Postman can be utilized without Burp. I have obtained a sample collection from Postman for this use case. I added variables to the parameters I wish to tinker with.
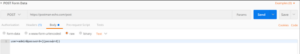
Figure 4: The body of the post request with the fuzz able password parameter
Figure 5: An example of a GET request with a fuzzed URL parameter
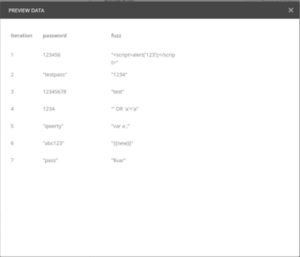
After we open the Collection Runner window, the Postman collection will be iterated in the following step. The test CSV file is chosen in the data section, with the GET parameter values and the password to be fuzzed. Each iteration can fuzz a different number of parameters, and the data file can be in either JSON or CSV format. The Collection Runner will pass each row of the data file during each iteration, searching for and replacing any variables in the API requests before submitting the requests. If only a few specific parameters in a limited number of requests need to be injected, the runner will transmit all the requests in the collection. It is preferable to gather the requests into a collection.
Figure 6: The variables for each iteration are displayed in a preview of the data file “test.csv.”
Example – test.csv
Figure 7: A console view displaying the API queries made during each iteration and their associated values
How To Implement HMAC In Postman?
API queries are often authenticated using the HMAC – Hashed Message Authentication Code. Due to the need for the secret to be added to the client-side code, this method is typically utilized in kiosk-to-server or server-to-server connections.
When Hash = Hashfunction(message+secret), Each request typically includes a signature header with the base64-encoded Hash value. The API requests won’t be approved without this header.
Several built-in modules are available in the Postman Sandbox JS environment for use by scripts in the Pre-request Script. The whole list of JavaScript libraries that are accessible may be found at –
https://www.getpostman.com/docs/v6/postman/scripts/postman_sandbox_api_reference
The message string in the following HMAC implementation example is created by concatenating the timestamp, message body, and URL path. Environment.get can retrieve the hashing secret, which is kept as an environment variable (“secret”).
Message = path+body+timestamp; Hash = SHA256(message+secret); Signature Header = base64.encode(Hash).
Use the required function to use a JS library in the sandbox. It is also possible to view the request data from the script, such as the URL, Headers, and Body, but this is only possible in read-only mode; no changes can be made from the script. The script cannot access request variables from the pm. request. * only as their variable names, not as their values. The list of PM operations that the script can use is accessible at http://www.postmanlabs.com/postman-collection/index.html
Examples Of pm.request Functions:
Request URL path – pm.request.url.getPath(); Request Body –pm.request.body.toString();
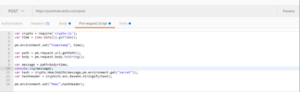
Pre-request Postman Script Example for HMAC Implementation
var crypto = require(‘crypto-js’); var time = (new Date()).getTime();
pm.environment.set(“timestamp”, time); var path = pm.request.url.getPath(); var body = pm.request.body.toString(); var message = path+body+time; console.log(message);
var hash = crypto.HmacSHA256(message,pm.environment.get(“secret”));
var hashHeader = CryptoJS.enc.Base64.stringify(hash); pm.environment.set(“hmac”,hashHeader);
Figure 8: HMAC Implementation Pre-request Script
Once the hash value has been determined, it is put to the request headers as Signature = {{“hmac”}} and set as an environment variable called “hmac.” The Postman console contains script errors that may be examined and utilized to debug the script.
Developers frequently use Postman to communicate with and test REST API. As we’ve demonstrated, it can also enable security analysis by supporting parameter fuzzing, logical API testing, and evaluating authorization and authentication implementations. Developers can share a set of API requests with security teams to help them plan a security test effort using the Collections function. Collections can also give API testers the test data and headers they need to send legitimate API queries. Additionally, Postman may proxy traffic through scanners and offer complete API security testing coverage. These are just a few examples of how Postman may be a helpful API security tool.
Summing up!
We have shared some of the useful insights of API security testing with POSTMAN, but if you think it will be a challenging task? Reach us now we have experts who can handle all your requirements efficiently and boost your store performance.

About Author
Tarun Bansal - Technical Head
Tarun is a technology enthusiast with a flair for solving complex challenges. His technical expertise and deep knowledge of emerging trends have made him a go-to person for strategic tech initiatives. Passionate about innovation, Tarun continuously explores new ways to drive efficiency and performance in every project he undertakes.