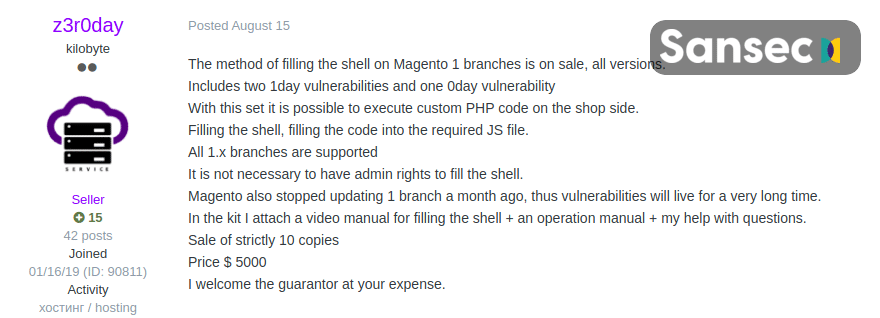
A massive cyber-attack happened against almost 2,000 Magento stores last weekend which is considered as the largest attack of its kind since 2015. It was a Magecart campaign that has compromised the private information and personal confidential details of thousands of customers.Though cybercriminals have used typical Magecart methods, it is believed that a new attack method was implemented to get server access to victimized stores. It was concluded as many victimized stores were never faced such security attacks before. It was first discovered by Sansec researchers. Furthermore, they also said that the campaign might be related to a recent Magento 1 zeroday exploit. Before a few weeks ago, it was put up for sale.Ameet Naik, security evangelist at PerimeterX said, “Magento 1.0 sites remain an attractive target for hackers looking to steal logins, personal data and financial data. This version no longer receives software updates as of June 2020, leaving sites exposed to zero day vulnerabilities such as the one that was exploited in this attack.”Sansec said in the blog that cybercriminals are coming up with new, advanced and innovative techniques to attack as it was seen in this incident. They are automating their hacking operations to run web skimming schemes on as many stores as possible.Further, Sansec also stated that a user named z3r0day has declared to sell a Magento 1 Remote Code Execution” exploit method with the instruction video for $5,000 on a hacking forum. The seller z3r0day also stated that no official patches will be provided by Adobe to fix this bug as Magento 1 is outdated. It renders this exploit extra damaging to store owners who are using the legacy platform.Sansac updated the same blog and came with information that the attackers “used the IPs 92.242.62.210 (US) and 91.121.94.121 (OVH, FR) to interact with the Magento admin panel and used the “Magento Connect” feature to download and install various files, including a malware called mysql.php.” The file was then automatically deleted once the malicious code had been added to prototype.js.
[Image: SanSec]
The researchers also wrote that a skimmer loader was added to prototype.js with payments “exfiltrated to a Moscow-hosted site at https://imags.pw/502.jsp, on the same network as the mcdnn.net domain.”A private advocate with Comparitech, Paul Bischoff discussed the security vulnerabilities of Magento 1 in detail. He added that “Hackers can easily scan for outdated versions of Magento and use automated bots to access them, upload shell scripts, and install the card skimming malware,”If you are still functioning on this outdated Magento 1 version, it is the time to upgrade to the latest version of Magento, called Magento 2. Paul further explained the same by stating, “Card skimming attacks are undetectable by end-users, so the responsibility falls on website operators to update their systems to the latest version of Magento. At this point, any website using Magento 1.x should be assumed compromised.”
Information Source: https://www.scmagazine.com/

About Author
Dipak Patil - Delivery Head & Partner Manager
Dipak is known for his ability to seamlessly manage and deliver top-notch projects. With a strong emphasis on quality and customer satisfaction, he has built a reputation for fostering strong client relationships. His leadership and dedication have been instrumental in guiding teams towards success, ensuring timely and effective delivery of services.
 [Image: SanSec]
[Image: SanSec]

